Phishing isn’t new, and it likely won’t be going anywhere any time soon.
It continues to be one of the primary attack vectors for tricking victims into opening the door for the bad guys. Although phishing adopts various guises, the most common example is where an email is received that contains spurious links and/or attachments, the accompanying text of which tries to entice the victim into clicking/opening said link or attachment.
You’ve got mail
There’s a fair chance that those of us nowadays who have any interaction with a computer in our day jobs (and many who don’t) will probably have at least heard the term ‘phishing’. I’d be willing to bet that the vast majority of people who have an email account have received phishing attempts, whether they realised it or not. A fair few of you will have seen the usual red herrings…
Congratulationns! You’ve won the lottary! $5,000,000 is waiting you in federal reserves. To claim send $5,000 here
Hi, Thanks for reviewing this
. Your reward will be sent soon.
Dear user, We are investigating a phishing scam.We have closed your account to prevent any unauthorised access. Click here to re-activate
Yes, the typo’s and grammar in the first example were intended, and the last one always makes me chuckle when it comes from an institution I have no affiliation with!
This post therefore aims to identify a few of the tell tell signs in phishing emails from a few random companies that a significant number of people have probably dealt with, these being Amazon, Santander and HMRC. They weren’t chosen for any particular reason other than they were obtained recently and seemed suitable. Please note that the areas discussed are not specific to these companies only and can often be found in general phishing emails however, they do provide some insight into how attackers think when attempting to emulate the vendors shown.
Each example has been highlighted to show fraudulent indicators however, these are by no means exhaustive. A discussion around the artefacts identified can be found after each visual example and at the end some contact details if you think you’ve received a phishing email from them.
Amazon
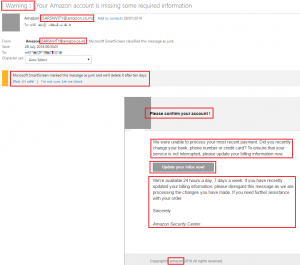
Where to start… Amazon won’t start an email subject with “[Warning!]”. Most companies won’t use punctuation or emotive language for a greeting so that’s something to watch out for. The sender email address is next. Anything coming from Amazon will always end in either .amazon.com or .amazon.co.uk, so .amazon.co.m should raise an eyebrow! Next is the Microsoft SmartScreen message. If your web mail provider’s own anti-virus/email security flags an email as being potentially malicious it’s almost a freebie! That’s not to say legitimate correspondence doesn’t end up flagged or in Junk sometimes but in cases such as these, it’s worth contacting the company to ascertain if an email was in fact sent and if so whether they think it could have ended up in Junk mail. More often than not it won’t be legitimate.
The title ‘Please confirm your account!’ is very informal and uses punctuation. The main body of text asks the question, “Did you recently change your bank, phone number or credit card?”. Amazon would know if you did and would never ask questions in an email. You may have noticed that the last sentence in the email isn’t even a complete sentence! “If you need further assistance with your order.” …. email us? call this number!? don’t hesitate to contact us anytime?!?! Even when the spelling is correct, grammar often isn’t.`
Then there’s the imposing “Update your infos now!” link. The grammatically incorrect shorthand is of course what jumps out here. The phish-detecting connoisseurs among you may think that Amazon wouldn’t ask you to update your information via a link however, to the less technical this may seem reasonable, so assuming you had suspicions from other artefacts discussed you’d hopefully be sceptical enough to hold fire on clicking.
The lower case ‘a’ in the copyright section at the bottom is indicative of a phishing attack. Companies like Amazon are pretty good at English and anything that references legal notation wouldn’t be amazon, it would be Amazon. Depending on the context of the email, Amazon may either not show any legal details, or the following will be present:
Amazon EU société à responsabilité limitée, 5 rue Plaetis, L-2338 Luxembourg. Share capital: EUR 37,500. RCS Luxembourg Number: B 101818. Business License Number: 134248. Luxembourg VAT Registration Number: LU 20260743.
They may or may not also have the following shown at the bottom of their emails:
Please note: This e-mail was sent from a notification-only address that can’t accept incoming e-mail. Please do not reply to this message.
One or both off these could of course be fraudulently included to increase credibility, however detecting phishing emails is all about building a profile of the evidence that will hopefully result in an educated decision.
A table of the types of legitimate Amazon email can be found below, along with their corresponding greetings and sign off’s. This is not necessarily an exhaustive list.
| Type of email | Sender address | Greeting | Sign off |
|---|---|---|---|
| Your Amazon.co.uk order of “item” | auto-confirm@amazon.co.uk | Hello, | We hope to see you again soon. Amazon.co.uk |
| An Amazon Gift Card you sent has been received | auto-confirm@amazon.co.uk | Greetings from Amazon.co.uk | None |
| Your order with Amazon.co.uk (gift card) | auto-confirm@amazon.co.uk | None | Thank you for shopping at Amazon.co.uk! |
| Your Amazon.co.uk order has been dispatched | auto-shipping@amazon.co.uk | Hello, | We hope to see you again soon. Amazon.co.uk |
| Your Amazon.co.uk order is out for delivery | order-update@amazon.co.uk | Hello, | We hope to see you again soon. Amazon.co.uk |
| Delivery of your Amazon.co.uk order “ref number” | order-update@amazon.co.uk | Hello, | We hope to see you again soon. Amazon.co.uk |
| Your return of “item” | return@amazon.co.uk | Hello, | None |
| Your refund for “item” | return@amazon.co.uk | Hello, | None |
| Your Prime Free Trial Membership Confirmation | prime@amazon.co.uk | Hello, | Thanks, The Amazon Prime Team |
Santander
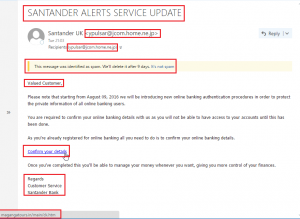
This is an example of a fraudulent Santander Alerts email. Santander, like most banks, won’t sent an email subject in full capital letters. If you ever see a subject in full caps or with a sense or urgency / punctuation at the end (!) then it’s likely a scam. The sender email address couldn’t be anything further from a legitimate Santander address. As before the web mail filter flagged the message as spam, a quick identifier that should never be overlooked. The salutation ‘Valued Customer’ is again suspicious as they will always address you by name, in one form or another.
With the exception of marketing related messages you won’t see links inside Santander emails. In the example depicted above the mouseover identified the actual URL that would be visited if the link was clicked (highlighted in the very bottom left) and it’s clearly nothing to do with Santander.
Next is the sign off (i.e. Kind regards, yours sincerely etc) which again has been seen to vary depending on the correspondence. A table of legitimate Santander email addresses, greetings and sign off’s can be found below, however this list is not necessarily exhaustive.
| Type of email | Sender address | Greeting | Sign off |
|---|---|---|---|
| New statement/communication (credit card/e-doc) | e-Documents@santander.co.uk | Dear Title full name | None |
| New statement/communication (banking/savings) | e-Documents@santander.co.uk | Dear Title full name | Kind regards, The Santander Online Banking Help Team |
| Alerts Service | e-Documents@santander.co.uk | Dear Title full name | Regards, Santander |
| Apple pay setup confirmation | applepay@santander.co.uk | Dear Title full name | Kind Regards, Santander |
| Marketing | santander@service.yoursantander.co.uk | Dear title surname | None |
| Credential reset/activation | customerservices@santander.co.uk | Dear title surname | Yours Sincerely printed signature Colin Webb, Director of Contact Centres |
| FSCS Communication | Donotreply_FSCS@santander.co.uk | Dear title surname | Yours Sincerely printed signature Reza Attar-Zadeh, Head of Retail Products |
| Switching to Santander | switcherupdate@santander.co.uk | Dear title surname | Kind Regards, The Santander Team |
Please note that the aforementioned names may vary depending on location. Another point to consider is that at the very top of most emails (research has shown all except alerts service ones), you will either see:
- This email is intended for title full name, partial postcode
- This email is intended for title surname, partial postcode
At the bottom of every email you will see the following with the exception of marketing emails, where the below is paraphrased a little with some extra information about the retail offers shown in that particular email.
This message was sent to you as a Santander customer, to tell you about important information concerning your account.
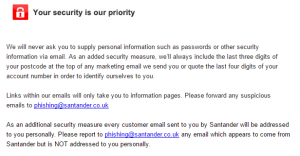
Please do not reply to this email. It has been sent from an email address that does not accept incoming emails. Santander will never ask you to supply personal information such as passwords or other security information via email. As an additional security measure, every customer email will be addressed to you personally. If you receive an email from Santander which is not personally addressed to you, or an email requesting personal information, please report this to phishing@santander.co.uk.
Santander UK plc. Registered Office: 2 Triton Square, Regent’s Place, London, NW1 3AN, United Kingdom. Registered Number 2294747. Registered in England. www.santander.co.uk. Telephone 0870 607 6000. Calls may be recorded or monitored. Authorised by the Prudential Regulation Authority and regulated by the Financial Conduct Authority and the Prudential Regulation Authority. Our Financial Services Register number is 106054. Santander UK plc is also licensed by the Financial Supervision Commission of the Isle of Man for its branch in the Isle of Man. Deposits held with the Isle of Man branch are covered by the Isle of Man Depositors’ Compensation Scheme as set out in the Isle of Man Depositors’ Compensation Scheme Regulations 2010. In the Isle of Man, Santander UK plc’s principal place of business is at 19/21 Prospect Hill, Douglas, Isle of Man, IM1 1ET. Santander and the flame logo are registered trademarks.
You can check this on the Financial Services Register by visiting the FCA’s website www.fca.org.uk/register or by contacting the FCA on 0800 111
Finally, Santander also includes information about how to spot potential phishing emails and how to contact them! With the exception of the alerts service emails and the ‘switching to Santander’ email which you’d only get when moving to them, you’ll also see the below in legitimate emails.
HMRC
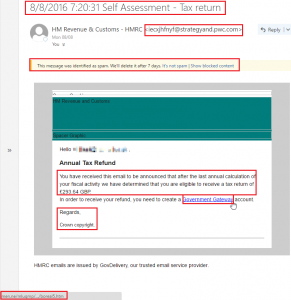
Much of the same applies here as can be seen by the respective highlighted areas. Even if HMRC did use an email subject like this, there’s a very good chance the recipient wouldn’t have carried out a self assessed tax return in the first place. The email is laughable and the web mail filter again flagged it as spam. The URL visited should the link be clicked (shown again in bottom left corner) looks totally fake and the sign off is nothing like HMRC.
HMRC themselves say they never use email to ask about a rebate or penalty however, if someone were to look solely at the link and Google ‘Government Gateway’ account for HMRC as a means of validation, they would find it’s both a valid type of account and valid terminology so all factors must be considered before jumping the gun.
I should note that the footer of the email…
HMRC emails are issued by GovDelivery, our trusted email service provider
…was a little tricky to identify. GovDelivery is both a legitimate organisation that specialise in public sector communications integration, and are also associated with HMRC. Despite the phishing example shown above, I was unable to find any concrete information as to whether that’s a valid email footer used anywhere within the organisation (tweet us @4ARMED if you know). The thing to note is that the value lies in aggregation and emails should be judged on the overall picture. Potentially one or two legit artefacts doesn’t make the email legit. It just means that attackers are trying to be a little more creative to try and increase the chances of that all elusive click.
A reference table like the ones in the aforementioned examples wasn’t really an option here, as I was unable to find a large quantity of legitimate HMRC emails to provide a legitimate frame of reference! By now however you’ll have an idea for the types of things to watch out for.
Received suspected phishing email from the above?
You can contact the vendors including the email using the following address:
- Amazon - stop-spoofing@amazon.com
- Santander - phishing@santander.co.uk (you can download their PDF on phishing here)
- HMRC - phishing@hmrc.gsi.gov.uk (this link shows known fraudulent email addresses used for HMRC phishing scams)
Final thoughts…
As you’ll probably have noticed all of the examples covered here were flagged by the web mail filter. The important takeaway is that the absence of filter identification does not in any way mean the email is legit. To re-iterate again, the value lies in aggregation. We need to make sure that we can identify the differentiating factors, both legitimate and suspicious, in order to derive the overall likelihood of authenticity. In many cases if absolutely everything about an email looked legit with the single exception of a link, that when moused over showed the URL www.h4x-s3rv3r.cx.cc, I’d still be willing to bet it was malicious.
Phishing scams are intrinsically connected to social engineering and the ability for an attacker to effectively ‘hack the user’ rather than the computer. The best defence for this type of attack is to embed within your company a strong and solid cyber security awareness culture, which often comes from both general individual assertiveness and effective training.
4ARMED has a free PDF download detailing “the EASY way” to reduce the chances of a successful phishing attack.
We also offer security awareness training so please get in touch if you wish to discuss your awareness training requirements.