This Wednesday an interesting collection of people gathered at the Royal College of Surgeons in London. The annual CREST conference gathered Penetration testers and security professionals from across the United Kingdom to discuss the current state of the industry.
The focus of the day was around targeted attacks (or Advanced Persistent Threats – APT) that have rocked the world recently, and what the security industry can do to help clients. This broadly split into two categories: How can we respond to and defeat the attackers, and how can we prepare our clients for these attacks?
What is an APT?
An Advanced Persistent Threat (APT) is an individual or group who use advanced digital capability to infiltrate networks in order to steal data and trade secrets. These groups will try to remain undetected through honed tradecraft and stealthy tools. Typical groups include “APT1” – Unit 61398 of the Chinese People’s Liberation Army.
The day kicked off with a talk from Mandiant covering the response issue. The field of Digital Forensics and Incident Response is growing enormously, and Mandiant shed a light on incident response on a global scale.
This theme of incident response was carried on by Context security in a talk and demonstration of their tool ‘RDP-Relay’. Whilst on a client engagement, a malicious actor was discovered to be using the Remote Desktop service to move throughout the client network. Some work from Context resulted in a tool capable of showing the attacker’s mouse and desktop in real time. This visual demonstration was apparently very effective in motivating the client board to remediate the threat.
All of these talks demonstrate that, “You can’t defend. You can’t prevent. The only thing you can do is detect and respond.” (Bruce Schneier). However, the defender has the advantage in that they can choose to prepare the battlefield (their network) to their advantage.
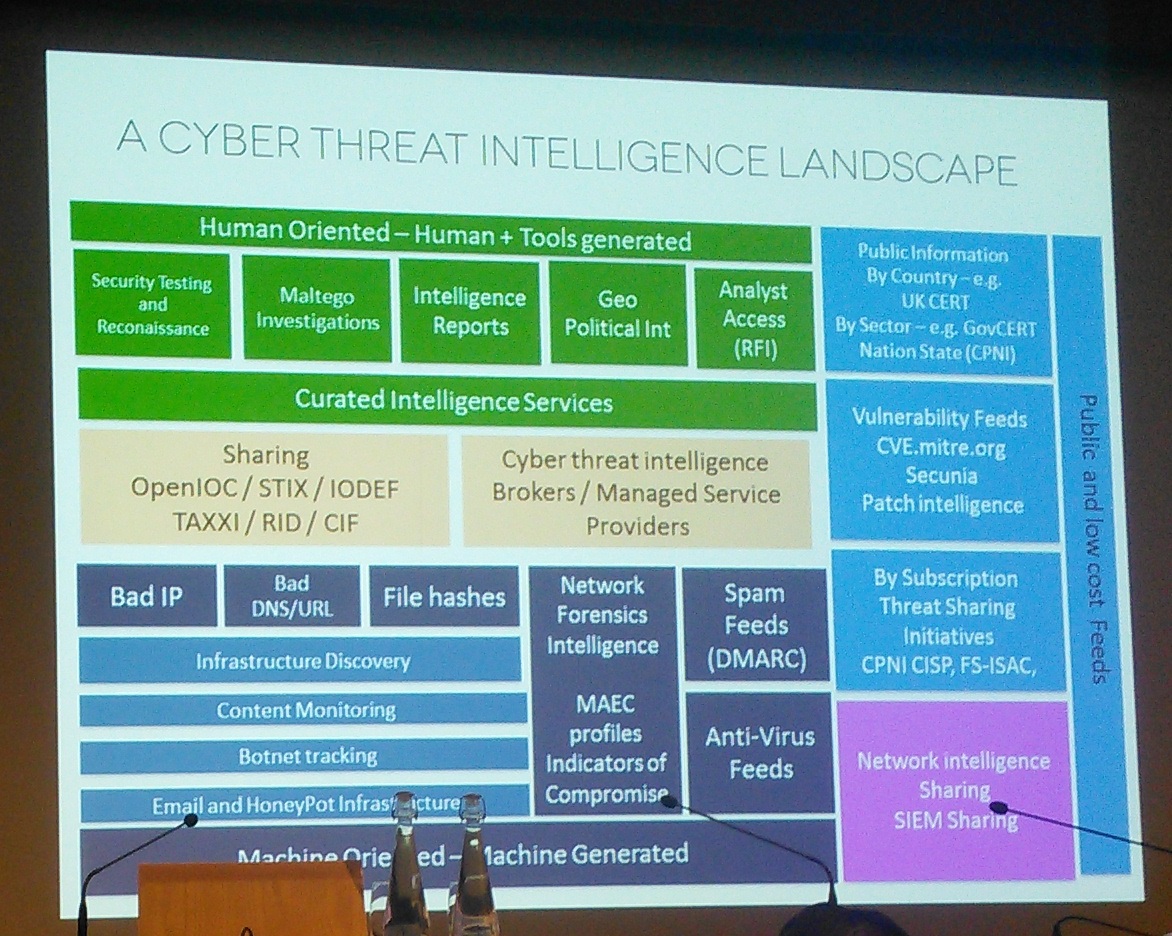
The second theme of the day considered how penetration testing can prepare clients for targeted attacks. This involves using intelligence about the threats to drive and tailor a penetration test.
What is Threat Intelligence?
Threat intelligence is information that can be analysed to give relevant and sufficient understanding to mitigate a harmful event (the Threat). Within digital security, this could include attacker’s IP addresses, attacker tools and attacker Tactics, Techniques and Procedures (TTPs). These allow defenders to anticipate and respond to an attack.
BAE systems Applied Intelligence division opened the debate with a talk on using attacker capability to provide testing. Using information from their internal Threat Intelligence group, the penetration testing group could tailor their tests to impersonate specific threat actors that they have seen in the wild, actively attacking clients.
One of the suggestions was to reverse engineer adversary tools and malware, then modify it and use it on client engagements. This raised numerous questions, including whether you could ever be sure of the malware being ‘safe’, and whether the original writer still had copyright. Whilst it seems farcical for a ‘black hat’ hacker to sue BAE systems for stealing their malicious code, all eventualities have to be considered.
For the day as a whole, the message is that both ‘Blue’ (Defense) and ‘Red’ (Offense) teams have to work together in order to prepare for targeted attacks. By using adversary Techniques, Tactics and Procedures we can mentor and train client defensive teams to detect and respond to advanced threats. This means when the attackers come knocking, they’re ready.